CredSSP Encryption Oracle Remediation
There is a critical security vulnerability found in the Credential Security Support Provider protocol (CredSSP) that could potentially lead to remote code execution. This vulnerability allows an attacker to intercept and relay user credentials, enabling them to execute malicious code on the targeted system.
CredSSP serves as an authentication provider for various applications, making any application reliant on CredSSP susceptible to this type of attack.
For instance, an attacker could leverage this vulnerability to exploit Remote Desktop Protocol (RDP) sessions by running a specially crafted application and conducting a man-in-the-middle attack. By doing so, the attacker gains the ability to install unauthorized programs, access, modify, or delete data, or even create new user accounts with complete privileges.
To address this critical issue, a security update has been developed to rectify the authentication process in the Credential Security Support Provider protocol (CredSSP). This update ensures the proper validation of authentication requests, effectively mitigating the vulnerability and safeguarding systems from potential exploitation.
1. SCENARIO
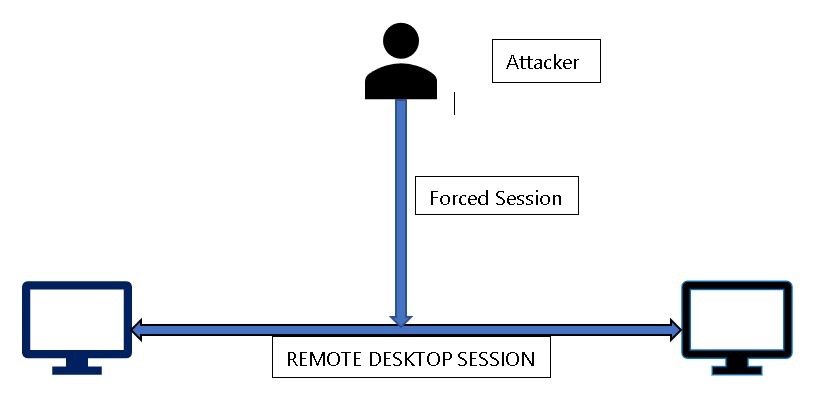
2. RDP SESSION
An update released by Microsoft (KB 4093492) on May 8, 2018, for Windows 10 Operation System was targeted to change the default settings CredSSP from Vulnerable to Mitigated.
A full list of the update and patches for all platforms can be obtained from here.
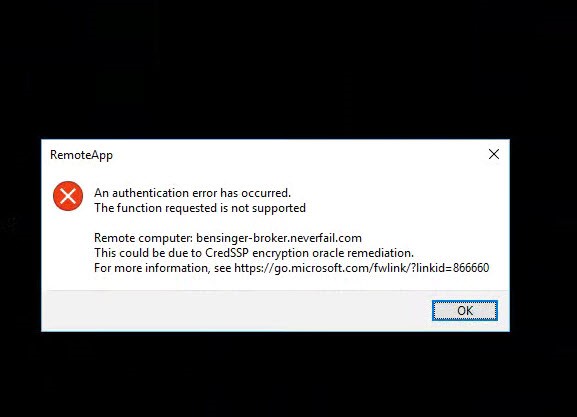
However, post patching this caused an issue where the patched clients were blocked from communicating with unpatched servers over RDP protocols.
This has been reported to cause an error thrown by Windows RDP as below:
3. WORKAROUND
Use the group policy settings changes described below to rollback the changes to ‘Vulnerable’ state to allow RDP access.
- Open Group Policy Editor, by executing gpedit.msc
- Policy path: Computer Configuration -> Administrative Templates -> System -> Credentials Delegation
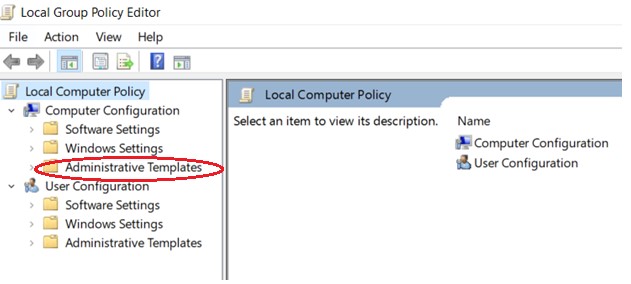
- Run gpedit.msc and expand Administrative Templates
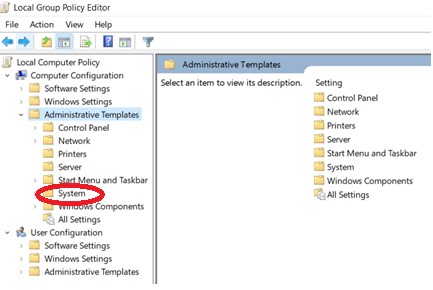
Expand System
Expand Credential Delegation
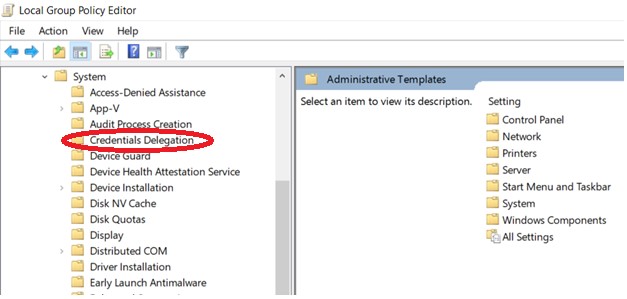
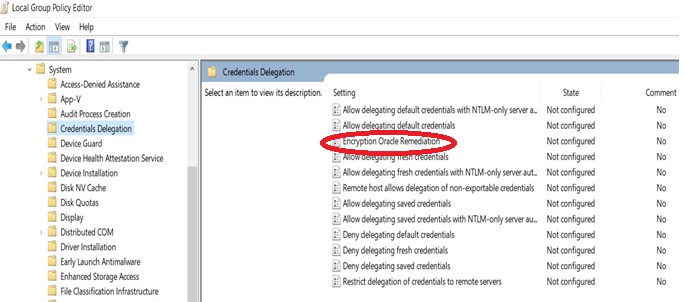
Edit Encryption Oracle Remediation
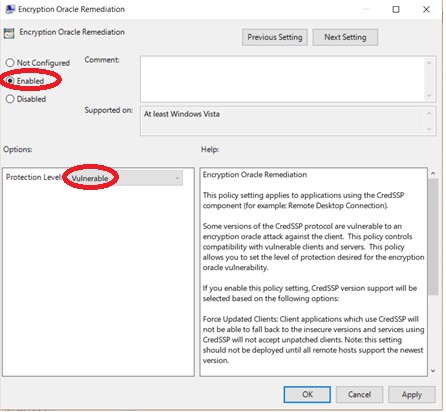
Select Enabled and change Production Level to Vulnerable
3. Run the command gpupdate /force to apply group policy settings.
4. Your remote desktop connection will be working fine now.
CONCLUSION
This is just a workaround and defeats the purpose of the patching. However, we need to ensure that future updates are installed as and when released by Microsoft so that the vulnerability is not exposed. Please let us know if this has solved your error.